Crypto investors have been moving their assets away from crypto exchange HTX (formerly known as Huobi) following a Nov. 22 exploit that saw the exchange pause its services and lose a total of $30 million.
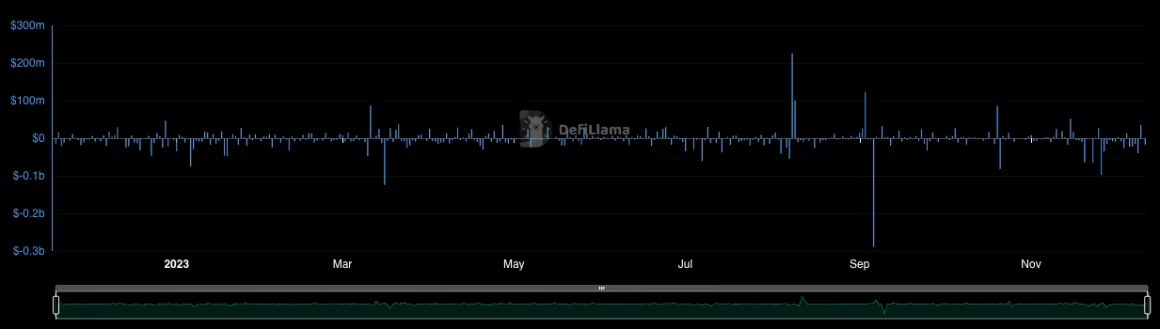
Between Nov. 25 — the day that HTX resumed its services — and Dec. 10, the exchange witnessed some $258 million in net outflows, according to data from DefiLlama.
DefiLlama data shows HTX’s reserves comprise 32.3% Bitcoin and 31.8% Tron. TRX is the native currency of the Tron network, a blockchain launched by Sun in 2017.
At the time of publication, HTX is the 16th largest crypto exchange by daily trading volume, with a total of $1.6 billion in trading volume in the last 24 hours, per CoinMarketCap data.
Following HTX’s restart on Nov. 25, Sun promised any affected HTX users that they would be fully compensated for the hot wallet losses and said a probe was underway.
HTX and Heco Cross-Chain Bridge Undergo Hacker Attack. HTX Will Fully Compensate for HTX's hot wallet Losses. Deposits and Withdrawals Temporarily Suspended. All Funds in HTX Are Secure, and the Community Can Rest Assured. We are investigating the specific reasons for the hacker…
— H.E. Justin Sun🌞(hiring) (@justinsuntron) November 22, 2023
Over the past two months, HTX and other Sun-linked entities, such as crypto exchange Poloniex and the HTX Eco Chain (HECO) bridge, have been hacked a total of four times.
The first HTX hack occurred less than two weeks after the exchange rebranded itself to HTX, with an unknown attacker stealing nearly $8 million in crypto on Sept. 24, 2023.
The largest of the exploits was the $100 million Poloniex exchange exploit on Nov. 10, allegedly caused by a private key compromise.
HTX’s HECO Chain bridge — a tool designed for moving digital assets between HTX and other blockchain networks — also suffered a massive breach on Nov. 22. Hackers compromised HECO and sent at least $86.6 million to suspicious addresses.
Meanwhile, November was the worst month for crypto theft this year, with hackers and other malicious actors making off with $363 million of ill-gotten digital assets.
Source: https://cointelegraph.com/news/crypto-exchange-htx-outflow-258-million-hack-november