Security researchers have discovered a troubling new method that hackers can use to extract private keys from a Bitcoin hardware wallet even with only signed two transactions, which they’ve named “Dark Skippy.”
The vulnerability potentially affects all hardware wallet models — though it can only work if the attacker tricks the victim into downloading malicious firmware.
A previous version of the method required the victim to post “dozens” of transactions to the blockchain. But the new “Dark Skippy” version can be performed even if the victim only posts a couple of transactions to the blockchain. In addition, the attack can be executed even if the user relies on a separate device to generate seed words.
The disclosure report was published by Lloyd Fournier, Nick Farrow, and Robin Linus on Aug. 5. Fournier and Farrow are co-founders of hardware wallet manufacturer Frostsnap, while Linus is a co-developer of Bitcoin protocols ZeroSync and BitVM.
According to the report, a hardware wallet’s firmware can be programmed to embed portions of the user’s seed words into “low entropy secret nonces” which are then used to sign transactions. The resulting signatures get posted to the blockchain when transactions are confirmed. The attacker can then scan the blockchain to find and record these signatures.
The resulting signatures contain only “public nonces,” not the portions of seed words themselves. However, the attacker can enter these public nonces into Pollard’s Kangaroo Algorithm to successfully compute the secret nonces from their public versions.
Pollard’s Kangaroo Algorithm, discovered by mathematician John M. Pollard, is an algorithm in computational algebra that can be used to solve the discrete logarithm problem.
According to the researchers, a user’s full set of seed words can be derived using this method, even if the user only produces two signatures from their compromised device and even if the seed words were produced on a separate device.
Previous versions of the vulnerability have been documented in the past, the researchers stated. However, these older versions relied upon “nonce grinding,” a much slower process that required many more transactions to be posted to the blockchain. Even so, the researchers stopped short of calling Dark Skippy a new vulnerability, claiming instead that it is “a new way of exploiting an existing vulnerability.”
To mitigate against the threat, the report suggests that hardware wallet manufacturers should take extra care to prevent malicious firmware from getting into users’ devices, which they can do through features like “secure boot and locked JTAG/SWD interfaces […] reproducible and vendor signed firmware builds[,…] [and] various other security features.” In addition, it suggests that wallet owners may want to employ practices to keep their devices secure, including “secret places, personal safes, or maybe even tamper-evident bags,” although the report also suggests that these practices may be “cumbersome.”
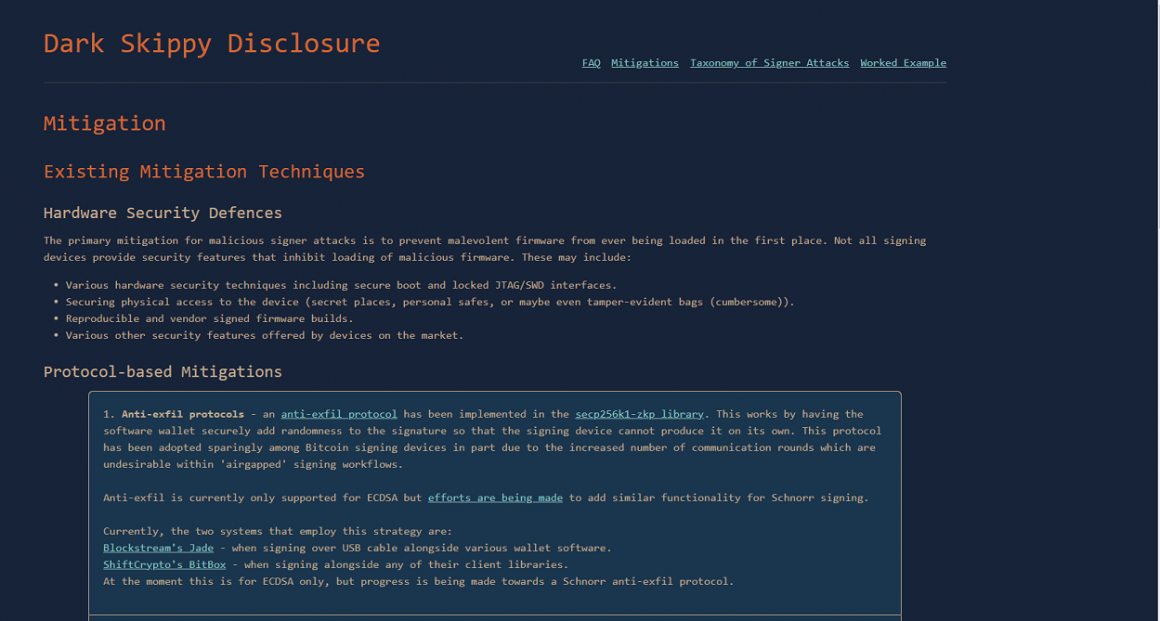
Another suggestion it provides is for wallet software to use “anti-exfiltration” signing protocols, which prevent the hardware wallet from producing nonces on its own.
Bitcoin wallet vulnerabilities have caused significant losses to users in the past. In August, 2023, cybersecurity firm Slowmist reported that over $900,000 worth of Bitcoin had been stolen via a flaw in the Libbitcoin explorer library. In November, Unciphered reported that $2.1 billion worth of Bitcoin held in old wallets may be in danger of being drained by attackers because of a flaw in BitcoinJS wallet software.
Source: https://cointelegraph.com/news/dark-skippy-method-can-steal-bitcoin-hardware-wallet-keys



