The role of a nonce in a blockchain
A nonce, short for “number used once,” is a special number that is assigned to a block in a blockchain during the mining process. It is an essential part of the proof-of-work (PoW) consensus mechanism.
The nonce, serving as a cryptographic puzzle, is a variable that miners manipulate to produce a hash value that satisfies particular requirements. Miners keep changing the nonce until they find a hash that possesses the necessary properties, which are frequently a set number of leading zeros. This iterative process, known as mining, ensures the security of the blockchain.
The correct nonce is essential for validating a block’s legitimacy and plays a pivotal role in block creation. It prevents malicious actors from tampering with data by making the computational effort required for such alterations prohibitively high.
The mining process is made more complicated by the trial-and-error method involved in determining the correct nonce. The block is deemed legitimate if miners discover the correct nonce, demonstrating the nonce’s crucial role in upholding the blockchain’s consensus, security and integrity.
The significance of a nonce in blockchain security
The nonce’s diverse function makes it extremely important for supporting blockchain security.
It is primarily important for preventing double-spending, which could jeopardize the integrity of digital currencies. The blockchain reduces the possibility of fraudulent manipulation by requiring miners to perform a computationally demanding process to discover a specific nonce. This assures that every transaction is uniquely confirmed.
Additionally, by placing a computational cost on attackers trying to take over the bulk of the network, the nonce adds to the defense against Sybil attacks. Malicious actors are discouraged by this strategy from flooding the system with fictitious identities.
Moreover, the nonce plays a significant role in maintaining the immutability of blocks. Any effort to change the content of a block requires recalculating the nonce, which is an impractical task that strengthens the blockchain’s integrity and resistance to tampering.
How is the nonce utilized in the Bitcoin blockchain network?
Miners use the Bitcoin nonce in a trial-and-error process to find a specific hash, meeting the network’s difficulty criteria, thereby validating and adding a new block to the blockchain.
The following step-by-step process explains how a nonce is calculated and used in Bitcoin mining:
- Block setup: Miners assemble a new block with pending transactions.
- Nonce inclusion: A unique nonce is added to the block header.
- Hashing attempt: Miners hash the block using SHA-256.
- Difficulty check: The hash is compared to the network’s difficulty target.
- Iterative process: Miners adjust the nonce until they find a hash meeting the difficulty, validating the block for addition to the blockchain.
The difficulty of finding a valid nonce in the Bitcoin blockchain is dynamically adjusted to maintain a steady block creation rate. To ensure miners, who compete to find the correct nonce for a valid block hash, face a challenge proportional to the network’s hashing power, this adaptive difficulty adapts to changes in network computational power.
The difficulty rises with network power, requiring more processing power to find an appropriate nonce. On the other hand, when the network’s processing capacity drops, the difficulty level also dwindles, making block creation easier.
What are the different types of nonce?
Nonces, whether cryptographic, hash function-related or programmatic, serve distinct purposes and aim to ensure data integrity in various computational applications.
While the concept is widely utilized in blockchain technology, various types of nonces exist across different applications. A prevalent type is the cryptographic nonce, which is employed in security protocols to thwart replay attacks by producing an exclusive value for every session or transaction.
Another type of nonce includes the cryptographic hash function nonce, which is used in hashing algorithms to alter the input nonce in order to alter the output hash. In programming, nonces can refer to values generated to ensure the uniqueness of data or to avoid conflicts.
Comprehending the particular context and objective is crucial since nonces take various forms, each designed to fulfill specific security or functionality needs in the wider field of computer science and cryptography.
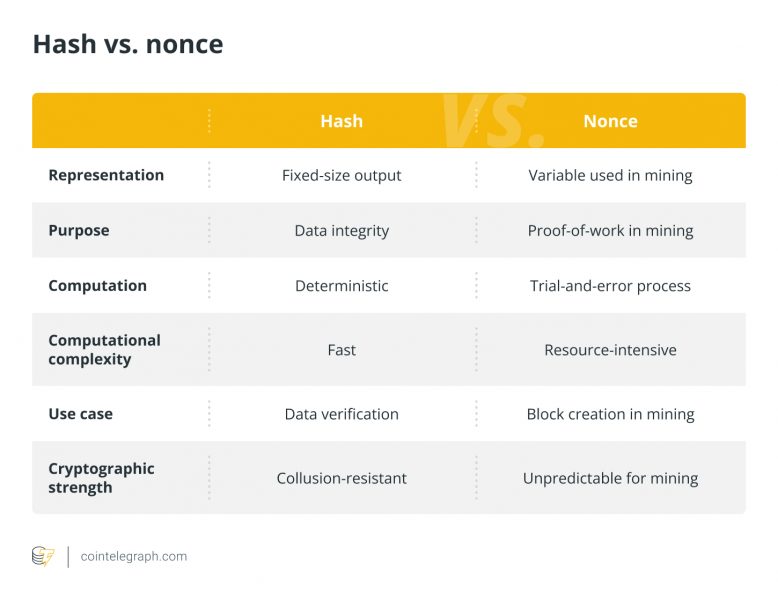
What is the difference between a hash and a nonce?
A hash is like a fingerprint for data, while a nonce is a special number used in the security puzzle of creating digital currency.
In the context of blockchain, a nonce is a variable that miners employ to produce hashes that satisfy certain requirements, whereas a hash is a fixed-size output produced from input data. The distinctions between hash and nonce are enumerated in the table below.
Nonce-related attacks in crypto and how to prevent them
In the field of cryptography, attacks involving nonces are mostly focused on taking advantage of flaws in the creation or management of nonces, particularly in cryptographic protocols.
One notable example is the “nonce reuse” attack, in which a malicious party is able to reuse a nonce during a cryptographic process, hence raising the possibility of security attributes being compromised. This is particularly significant for systems that depend on nonces to be unique, such as digital signatures and encryption.
The “predictable nonce” attack is another common attack in which adversaries can anticipate and manipulate cryptographic operations because nonces exhibit a predictable pattern. Furthermore, “stale nonce” attacks include tricking systems by using out-of-date or previously valid nonces.
Cryptographic protocols must ensure the uniqueness and unpredictable nature of nonces to prevent nonce-related attacks. Properly implemented random number generation is essential, ensuring that nonces have a low probability of repetition. Moreover, protocols should also incorporate mechanisms to recognize and reject reused nonces. Reusing nonces in asymmetric cryptography can have dangerous repercussions, such as disclosing secret keys or jeopardizing the privacy of encrypted communications.
Additionally, continual upgrades to cryptographic libraries and protocols, along with continuous observation for unusual trends in nonce usage, aid in the defense against ever-evolving attack vectors. Mitigating vulnerabilities related to nonces requires the use of security best practices, such as regular evaluation of cryptographic implementations and strict adherence to standardized cryptographic algorithms.
Source: https://cointelegraph.com/explained/what-is-a-nonce-in-blockchain-explained


